Denver Technology's Cyber Security Services address the increasing complexity and necessity of securing Operational Technology (OT) environments. Traditionally, OT environments were separated from corporate IT networks, simplifying their security. However, the growing convergence of Industrial Control System (ICS) environments with external digital infrastructures - such as remote access, data analytics, and corporate IT - has made securing these environments more complex and critical.
Our approach ensures the OT environment remains operational, safe, and secure. Our designs are aligned with the perdue network model and employs security devices (Firewalls), De-Militarised Zones (DMZs), controlled jump-hosts and appropriate Out-of-band management networks and monitoring.
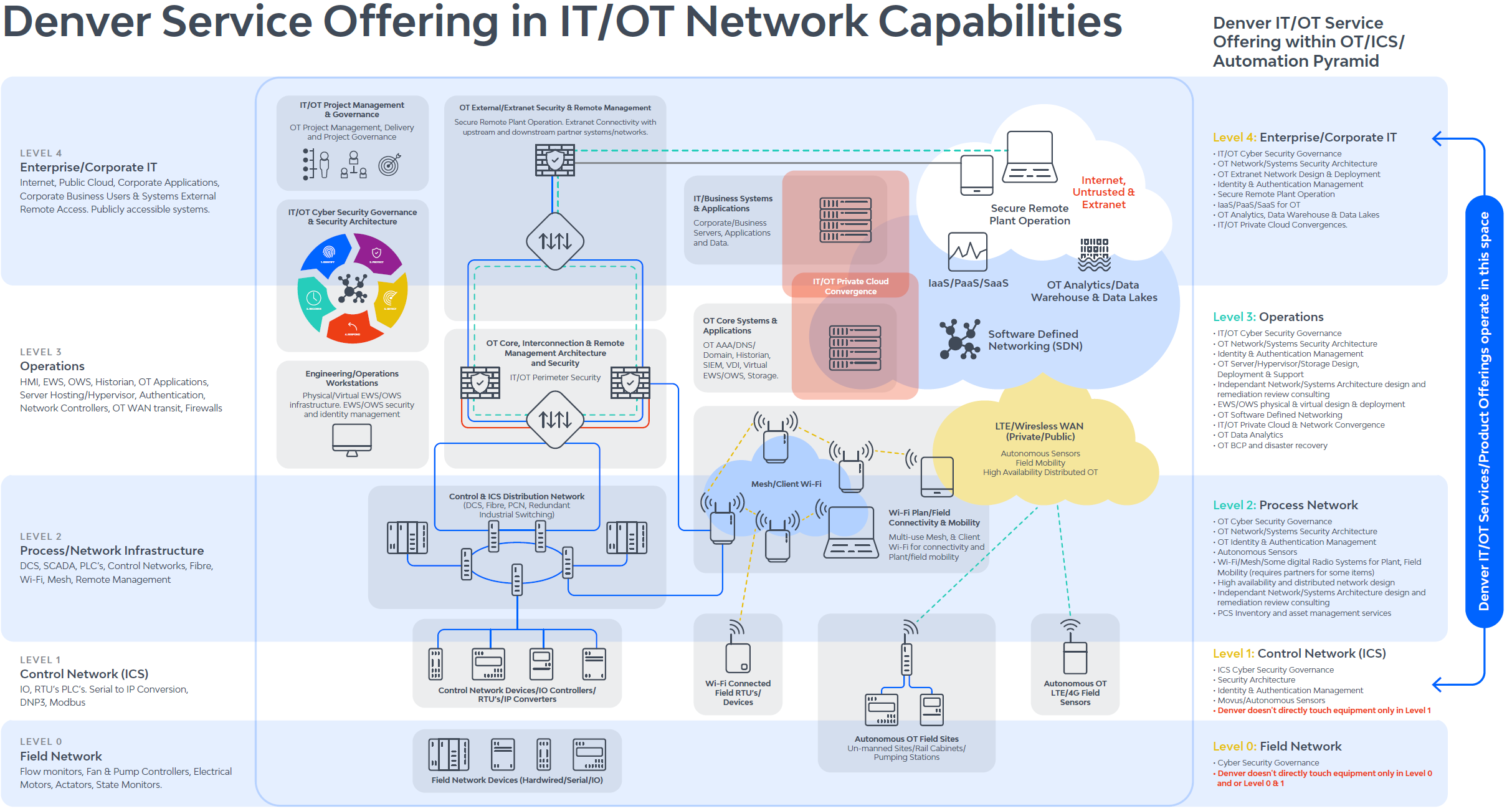
We help our clients address their Cyber Security strategy and governance issues with the following services:
Developing Risk & Compliance Security Policy Frameworks
We transform our clients' IT/OT strategies, roadmap objectives, and assessment priorities into robust security policy frameworks, ensuring that Cyber Security practices align with industry standards and support regulatory compliance.
Third-Party Solution Assessment
We assess proposed solutions from third-party vendors, providing oversight to ensure alignment with corporate standards and security requirements.
Enabling Secure Remote Management
We enable remote management of OT systems without compromising security, allowing for efficient and secure operations
Denver Technology excels in delivering premier cybersecurity solutions, leveraging a blend of extensive certifications and hands-on experience. Our team’s qualifications span both IT and OT environments, ensuring adherence to the highest standards of security and compliance. We specialise in addressing the unique challenges of asset-intensive industries like Energy and Resources, developing tailored solutions that protect sensitive data, mitigate risks, and enhance operational efficiency. By staying ahead of emerging threats and regulatory requirements, we ensure the continuous, secure operation of essential services for our clients.

Industrial Control System (ICS) Cyber Security Certifications & Qualifications
- DHS CISA (100W/200W/301V/401V):
- Cybersecurity Practices: Foundational and advanced knowledge.
- Incident Response: Effective handling of cybersecurity incidents.
- Vulnerability Assessment: Identifying and mitigating vulnerabilities.
- Modern SCADA Communication Systems (CDN-SP)
- Specialised Knowledge: Expertise in SCADA systems and secure communication protocols (DNP3, IEC60870).
- System Integration: Efficient integration with existing infrastructure, ensuring security and operational efficiency.
- Fundamentals of Industrial Control Systems (SAK9)
- Fundamentals of Industrial Control Systems (SAK9)
- Comprehensive Understanding: Essential for secure ICS design and maintenance.
- Operational Security: Protects critical infrastructure and ensures continuous operation.

Certified Information Systems Security Professional (CISSP)
The CISSP certification demonstrates a broad and deep understanding of information security. It covers various domains such as security and risk management, asset security, security architecture and engineering, communication and network security, identity and access management, security assessment and testing, security operations, and software development security.

Securing Your OT and ICS Environments: It’s a Cost and Safety Issue
When we think of cybersecurity, our first thoughts typically turn towards IT systems, databases, personal information, credit card information etc. But in mining and resources, you also need to think about the Operational Technology (OT) and Industrial Control System (ICS) environments – and these present a totally new set of challenges.

Securing OT Networks Beyond Guards, Guns & Gates
In this Insight, Denver Strategic Consulting Services Manager, Keren Jenns asks two of Denver's OT SME's to consider IT and OT convergence issues on manufacturing operations and look at how organisations are securing their operations beyond guards, guns and gates.

The Critical Need for Secure PCN in Mining, Oil & Gas
Process Control Networks are complex in design and implementation because they integrate with a range of corporate and industrial components. PCN's perform sensitive and vital tasks for managing and handling critical infrastructure. It’s imperative to implement security in these systems because they are targets for cyber-attacks.
